Understanding the Common Vulnerability Scoring System
Surviving a Global Cyberattack - Company Culture Plays a Pivotal Role
IA Targeted in Ethical Hacking Competition: What You Need to Know
Assessment of Ransomware Event at U.S. Pipeline Operator
Top Article for 2018 - Protecting Utilities
How to Keep Your Manufacturing Site Secure in the Age of the IIoT
How the Manufacturing Industry Can Defend Against Cyberattacks
Digital Transformations Carry Cybersecurity Concerns
The Industrial IoT Risks You Must Not Ignore in 2018
SCADAfence Secures $10 Million in Funding to Protect Smart Manufacturing and Critical Infrastructure Networks from Cyber Attacks
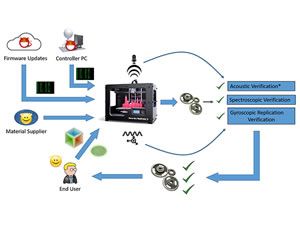
Defending 3D Printers From Hackers
The ioTrust Security Solution
IIoT And The CyberThreat: A Perfect Storm Of Risk
Why PKI matters for the IIoT
Cybersecurity in the Factory
Records 16 to 30 of 38
First | Previous | Next | Last
Featured Product